
Cyber threat modeling is a process that helps identify vulnerabilities, assess risks, and suggest corrective actions to improve cybersecurity and trust in key business systems. As organizations become more digital and cloud-based, IT systems face increased risk and vulnerability.
Growing use of mobile and Internet of Things (IoT) devices also expands the threat landscape. Threat modeling is a systematic and strategic approach for identifying and enumerating threats to an application environment. It involves the analysis of each aspect of the application’s functionality, architecture, and design. The process of threat modeling can be decomposed into three high-level steps: decompose the application, determine and rank threats, and determine countermeasures and mitigation.
There are several types of threat modeling methodologies available, including STRIDE, PASTA, CVSS, Trike, and Attack Trees. The choice of framework depends largely on an organization’s unique business, security, and regulatory needs and requirements.
Threat modeling is a cornerstone of effective cyber resilience, and no longer optional in today’s security landscape. It is important to identify and classify potential weaknesses that could lead to an exploit.
Threat modeling helps to create an abstract of the system and give reports of potential attackers, providing insights into potential vulnerabilities and threats that can arise in the future. The article focuses on the importance of cyber threat models, types of cyber threat models, and the cyber threat modeling process.
What are the main objectives of cyber threat modeling?
Objectives of Cyber Threat Modeling
Cyber threat modeling aims to identify, analyze, and mitigate potential cybersecurity threats within an organization’s IT environment. The primary objectives of cyber threat modeling include:
- Identifying vulnerabilities: Threat modeling helps to discover weaknesses in the system that could be exploited by attackers.
- Prioritizing threats: By understanding the potential risks, organizations can prioritize threats based on their likelihood and impact.
- Suggesting countermeasures: Threat modeling provides recommendations for addressing identified vulnerabilities and threats.
- Improving security posture: By implementing the suggested countermeasures, organizations can enhance their overall security posture.
- Reducing risk exposure: Threat modeling helps to minimize the risk of cyberattacks by identifying and addressing potential vulnerabilities.
- Collaboration: Threat modeling fosters collaboration between security architects, security operations, network defenders, SOC, and threat intelligence teams.
- Compliance: Threat modeling helps organizations to comply with data privacy and security laws and regulations.
- Documentation and reporting: Threat modeling provides a structured approach for documenting and reporting cybersecurity threats and their mitigation strategies.
These objectives are crucial for organizations to maintain a robust cybersecurity posture and protect their digital assets from cyber threats.
How does threat modeling help organizations prioritize cybersecurity needs?
Threat modeling helps organizations prioritize cybersecurity needs by identifying and quantifying potential threats, vulnerabilities, and risks. By understanding which threats require the most attention and resources, organizations can make informed decisions about where to allocate their security efforts and budget.
Threat modeling also helps to strengthen compliance with data privacy and security laws and regulations, such as the European Union’s GDPR. Threat modeling methodologies, like STRIDE, PASTA, TRIKE, and others, provide a structured approach for identifying and mitigating threats. These methodologies help organizations to:
- Document the system’s architecture, assets, and resources.
- Identify potential threats, their severities, and the likelihood of occurrence.
- Suggest countermeasures and mitigation strategies.
- Validate the model’s correctness and verify that fixes and patches are successful.
Threat modeling is a cornerstone of effective cyber resilience and should be performed regularly to ensure that organizations maintain a robust cybersecurity posture.
Cyber Threat Modeling Process?.

The Threat Modeling Process
Threat modeling is a systematic approach to identifying, analyzing, and mitigating potential cybersecurity threats within an organization’s IT environment. The process can be decomposed into five high-level steps:
- Decompose the Application: Understand the application’s functionality, architecture, and design by creating use cases, identifying entry points, and assets.
- Determine and Rank Threats: Use threat categorization methodologies like STRIDE to identify and prioritize threats based on their likelihood and impact.
- Analyze Vulnerabilities: Assess the application’s vulnerabilities and their potential exploitation by attackers.
- Assess Risks: Evaluate the risks associated with each threat and vulnerability, considering their likelihood and impact.
- Implement Countermeasures and Mitigation: Develop and implement countermeasures to address identified threats and vulnerabilities, ensuring a robust cybersecurity posture.
Examples of threat categorization methodologies include STRIDE, PASTA, CVSS, Trike, and Attack Trees. These methodologies help organizations to:
- Document the system’s architecture, assets, and resources.
- Identify potential threats, their severities, and the likelihood of occurrence.
- Suggest countermeasures and mitigation strategies.
- Validate the model’s correctness and verify that fixes and patches are successful.
Tools and techniques that support the threat modeling process include data flow diagrams (DFDs), threat trees, and risk assessment frameworks like NIST SP 800-30 and ISO 27001.
Best Practices for Identifying Assets
To identify critical and valuable assets, organizations can use criteria such as business impact analysis, risk assessment, and asset valuation. Best practices for identifying assets include:
- Utilizing multiple sources and methods, such as interviews, surveys, documentation, and tools.
- Updating and reviewing asset inventories regularly to ensure accuracy and completeness.
- Categorizing assets based on their type, function, location, owner, or lifecycle.
- Considering asset dependencies to avoid cascading issues if a critical asset fails.
Tools and Techniques
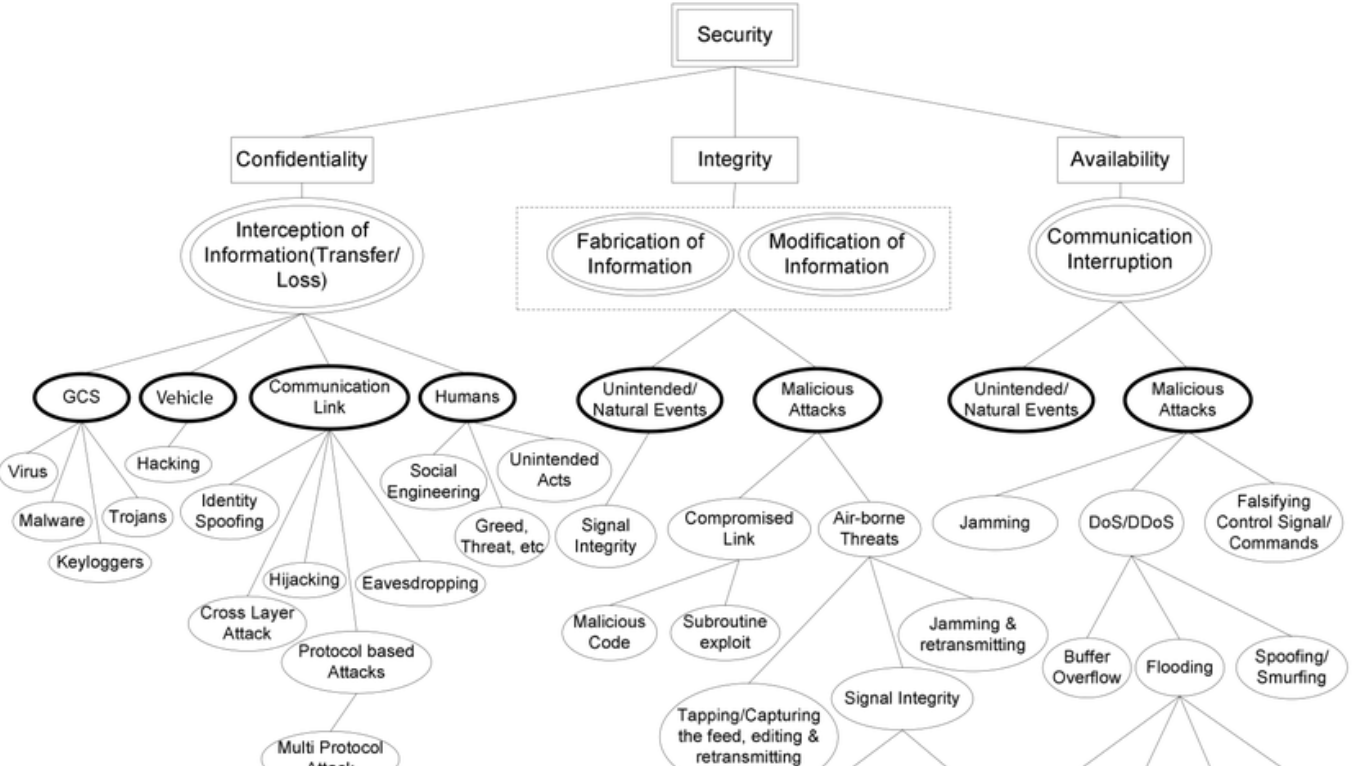
Threat modeling tools help security teams proactively discover and address potential security issues in devices, software, and data. Examples of threat modeling tools include:
- MITRE ATT&CK Framework
- OWASP Threat Dragon
- ThreatModeler by Synopsys
- ThreatAxe by Contrast Security
These tools help security teams structure security practices like penetration testing and threat modeling, improving an organization’s ability to identify threats and vulnerabilities.
Threat modeling is a crucial process for organizations to maintain a robust cybersecurity posture. By identifying, analyzing, and mitigating potential threats, organizations can prioritize their security efforts and ensure that their systems are secure.
The process involves five high-level steps: decompose the application, determine and rank threats, analyze vulnerabilities, assess risks, and implement countermeasures and mitigation. Tools and techniques like data flow diagrams, threat trees, and risk assessment frameworks support the threat modeling process, helping organizations to identify and address potential threats and vulnerabilities.
What are some examples of countermeasures that can be implemented during the threat modeling process?
Countermeasures in Threat Modeling
During the threat modeling process, organizations identify and prioritize countermeasures to address potential threats and vulnerabilities. Some examples of countermeasures include:
- Authentication: Implementing appropriate authentication mechanisms to ensure that only authorized users can access the system.
- Authorization: Ensuring that users have the necessary permissions to perform specific actions within the system.
- Encryption: Encrypting sensitive data to protect it from unauthorized access.
- Access control: Limiting access to specific areas or resources within the system based on user roles and permissions.
- Input validation: Validating user input to prevent malicious data from being processed by the system.
- Output encoding: Encoding output data to prevent cross-site scripting (XSS) attacks.
- Secure coding practices: Adopting secure coding practices to prevent vulnerabilities from being introduced during development.
- Secure configuration: Configuring systems and applications securely to prevent known vulnerabilities from being exploited.
- Monitoring and logging: Implementing monitoring and logging mechanisms to detect and respond to security incidents.
- Regular updates: Regularly updating software and systems to address known vulnerabilities.
These countermeasures help organizations to mitigate risks and protect their systems from potential threats. By implementing these countermeasures, organizations can improve their overall security posture and reduce the risk of cyberattacks.
What are Cyber Threat Modeling Methodologies?
Cyber threat modeling is a process that helps identify vulnerabilities, assess risks, and suggest corrective actions to improve cybersecurity and trust in key business systems.
There are several methodologies and frameworks available for cyber threat modeling, including:
Cyber Threat Modeling Methodologies
- STRIDE: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. STRIDE is a flexible and adaptable framework that can be applied across multiple industries. It is particularly useful for companies that have a clear understanding of the threats and vulnerabilities it faces. STRIDE is relatively easy to use but can be time-consuming. It primarily focuses on analyzing the system’s design and architecture, potentially missing dynamic or runtime threats.
- PASTA: Process for Attack Simulation and Threat Analysis. PASTA is a risk-centric threat modeling methodology that provides a step-by-step process for identifying and mitigating potential threats. It incorporates business impact, inherent application risk, trust boundaries among application components, correlated threats, and attack patterns that exploit identified weaknesses from the threat modeling exercises. PASTA is simple to implement because it is a static framework. However, with ever-evolving threat landscapes, it doesn’t make sense to have static threats across several industries.
- VAST: Visual, Agile, Simple Threat modeling. VAST is designed to support enterprise-wide scalability by encircling the entire software development life cycle (SDLC). It incorporates three necessary pillars: automation, integration, and collaboration, which makes it suitable for large-scale enterprises. VAST provides a comprehensive framework that considers business, application, and technology layers, offering a more holistic view of security. It contains built-in prioritization of threat mitigation and security controls or preventive measures are defined to address the threats.
- TRIKE: Threat Risk Identification and Knowledge-based Engineering. TRIKE is an open-source threat modeling process focused on the security auditing process from a risk management and defense perspective. This risk-based approach looks at implementation, threats and risk models, meaning it ensures the assigned level of risk for each asset is acceptable to its stakeholders. TRIKE provides a comprehensive framework that considers business, application, and technology layers, offering a more holistic view of security. It contains built-in prioritization of threat mitigation and security controls or preventive measures are defined to address the threats.
- CVSS: Common Vulnerability Scoring System. CVSS is a framework for rating the severity of security vulnerabilities in software. It provides a standardized method for assessing and communicating the severity of vulnerabilities, allowing organizations to prioritize their remediation efforts.
- Attack Trees: Attack trees are a graphical representation of the steps an attacker would take to achieve a specific goal. They are useful for identifying potential attack vectors and understanding the impact of different countermeasures.
Choice of framework
The choice of framework depends largely on an organization’s unique business, security, and regulatory needs and requirements. Each methodology has its advantages and disadvantages, and organizations should choose the most suitable methodology for a given context and scenario.
Some factors to consider when choosing a methodology include the organization’s size, complexity, and industry, as well as the level of expertise of the team performing the threat modeling. Tools and techniques that support the threat modeling process include data flow diagrams, threat trees, and risk assessment frameworks like NIST SP 800-30 and ISO 27001.
How does the pasta methodology differ from the stride methodology in terms of threat modeling?
PASTA vs. STRIDE: A Comparison of Threat Modeling Methodologies
STRIDE and PASTA are two popular threat modeling methodologies with distinct approaches and strengths.
a. STRIDE
- Focus: Categorizes threats into six categories: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege.
- Simplicity: Relatively easy to implement and understand, making it suitable for less complex systems or teams new to threat modeling.
- Proactive Defense: Encourages teams to anticipate and prepare for security threats, leading to more robust defenses.
- Use Cases: Ideal for system design, especially during the development phase of a software system or application.
b. PASTA
- Focus: A risk-centric methodology that incorporates business impact, inherent application risk, trust boundaries among application components, correlated threats, and attack patterns that exploit identified weaknesses.
- Comprehensiveness: Offers a more thorough analysis of potential threats, from identification to attack simulation and weakness analysis.
- Business-centric: Aligns security considerations with business goals by considering business objectives and related risks.
- Use Cases: Suitable for organizations that wish to align threat modeling with strategic objectives, especially for complex systems.
Choosing Between STRIDE and PASTA
The choice between STRIDE and PASTA depends on the organization’s specific needs, resources, system complexity, and overall security objectives.
- STRIDE is a good choice for less complex systems or teams new to threat modeling.
- PASTA is more suitable for organizations that wish to align threat modeling with strategic objectives, especially for complex systems.
- Both methodologies can be used together to create a more robust and comprehensive threat modeling framework.
Regular threat modeling is essential in any robust cybersecurity strategy, regardless of the methodology chosen. The combination of STRIDE and PASTA can lead to a more comprehensive and effective threat modeling framework.
Cyber Threat Modeling Applications and Case Studies?
Cyber threat modeling is becoming increasingly important as organizations face new and evolving threats in the digital age. Some of the current and future applications and trends of cyber threat modeling include cloud computing, IoT, AI, and blockchain.
For example, the expanding IoT creates more opportunities for cybercrime, while AI and machine learning are revolutionizing cyber security by automating tedious processes for identifying and addressing threats. Cyber threat modeling has been used in various domains and industries, such as healthcare, finance, education, and government.
For instance, in the healthcare sector, cyber attacks against hospitals have increased significantly, compromising patient safety. Lessons learned and best practices from case studies include embedding a culture of risk awareness and good cyber security, streamlining and simplifying the oversight and governance of cyber security and risk, and developing sustainable minimum cyber security standards for the design, build, and procurement of medical devices.
As the risk of cyber disruption increases, it is crucial for organizations to prioritize cyber threat modeling to maintain a robust cybersecurity posture.
How has the use of block-chain technology impacted cyber threat modeling in the finance industry?
The use of blockchain technology has had a significant impact on cyber threat modeling in the finance industry. Blockchain technology provides heightened security, improved transaction processes, ensures transparency and privacy, optimizes operational performance, and reduces fraud.
One of the most significant applications of block-chain technology is in streamlining payment systems. By eliminating the need for intermediaries, block-chain-based payment systems can facilitate faster, more secure, and more affordable cross-border transactions, reducing transaction fees and time delays.
Additionally, blockchain technology can improve asset security and management by providing a tamper-proof environment for secure transactions.
Block-chain technology can also facilitate compliance by providing a secure, transparent, and tamper-proof record of transactions, making it easier for regulators to monitor and audit financial activities.
The adoption of block-chain technology in trade finance can address challenges such as slow and cumbersome processes, extensive paperwork, and susceptibility to fraud.
The potential applications of block-chain technology in finance are vast and varied, and as more companies embrace this technology, we can expect to see further innovation and disruption in the industry moving forward.
What are some challenges that have been faced in implementing block-chain technology for cyber threat modeling in the finance industry?
The challenges faced in implementing blockchain technology for cyber threat modeling in the finance industry include:
- Security Breaches and Hacking: Despite the touted security measures of block-chain, there have been instances of security breaches and hacking attacks on block-chain networks, resulting in monetary losses and damage to the integrity of the network.
- Complexity: Block-chain is a complex technology that requires a high level of technical expertise to implement and maintain. This complexity may hinder the widespread adoption of block-chain technology and discourage potential users and developers.
- Interoperability: Interoperability, or the ability of different block-chain networks to work together, is a significant challenge. The lack of interoperability can make mass adoption of block-chain an almost impossible task.
- Regulatory Uncertainty: The lack of clarity about regulatory requirements creates significant risk for block-chain providers and consumers. This uncertainty can hinder the adoption of block-chain technology in the finance industry.
- Costs and Data Modification: The high costs of implementing block-chain technology, along with potential data modification problems, pose challenges for its adoption in the finance industry.
- User Acceptance and Trust: User acceptance of block-chain technology is a main factor and may be hampered by trust and comfort with fully automated systems. Dependence on computers and power makes the systems unreliable if something happens due to software or power failure.
- Resistance to Change: Resistance to change is a standard challenge in any enterprise, including banking. Workers and stakeholders are hesitant to adopt blockchain technology due to job relocation, uncertainty, or concerns about the reliability of the technology.
These challenges need to be addressed to ensure the successful implementation of blockchain technology for cyber threat modeling in the finance industry.
How can organizations ensure that their cyber threat modeling process is comprehensive and effective?
To ensure that their cyber threat modeling process is comprehensive and effective, organizations can take several steps. First, they should adopt a structured approach to threat modeling, such as using hypothetical scenarios, system diagrams, and testing to help secure systems and data.
This involves identifying vulnerabilities, helping with risk assessment, and suggesting corrective action. Second, organizations should consider using threat modeling methodologies and tools, such as STRIDE, PASTA, VAST, Trike, CVSS, Attack Trees, and hTMM, to improve the security of complex systems.
Third, they should embed a culture of risk awareness and good cybersecurity, streamline and simplify the oversight and governance of cybersecurity and risk, and develop sustainable minimum cybersecurity standards for the design, build, and procurement of systems.
Finally, organizations should consider using automated threat modeling tools to improve the accuracy and efficiency of the process. By following these recommendations, organizations can ensure that their cyber threat modeling process is comprehensive and effective, helping to improve cybersecurity and trust in key business systems.
Conclusion
In conclusion, cyber threat modeling is a crucial process for identifying vulnerabilities, assessing risks, and suggesting corrective actions to improve cybersecurity and trust in key business systems. The process involves identifying assets, identifying threats, analyzing vulnerabilities, assessing risks, and implementing countermeasures.
There are several methodologies and frameworks available for cyber threat modeling, including STRIDE, PASTA, VAST, Trike, CVSS, Attack Trees, and hTMM. Each methodology has its advantages and disadvantages, and the choice depends on the organization’s specific needs, resources, system complexity, and overall security objectives.
To conduct cyber threat modeling effectively and efficiently, organizations should embed a culture of risk awareness and good cybersecurity, streamline and simplify the oversight and governance of cybersecurity and risk, and develop sustainable minimum cybersecurity standards for the design, build, and procurement of systems.
Organizations should also consider using automated threat modeling tools to improve the accuracy and efficiency of the process. In conclusion, organizations must prioritize cyber threat modeling to maintain a robust cybersecurity posture and protect against evolving cyber threats.
4 thoughts on “What is a Cyber Threat Model Process for Information Security?”